Ever since COVID-19 took hold in early 2020, businesses across the globe had to figure out ways to increase their data security to counteract the increase in scams and hackers attacking businesses for their data, passwords, and details. With more of us than ever having to work from home offices, this has meant that security protocols and not always followed - and scammers have been quick to act.
In respect to this, what can you do to increase your data security protection in the 'new normal' world of COVID-19?
Skip to a section:
- Why The Increase of Data Security Threats?
- What Are These Threats?
- How To Identify a COVID-19 Phishing Threat
- Secure Your Data Like A Boss
- A Quick Fire Guide to Reducing Your Data Security Risk
- How Integration Fox Can Help You
First, let's define what data security is. In its simplest terms, data security is the process of protecting digital data (such as those in a company's database), from destructive forces and from the unwanted actions of unauthorised users such as a cyber attack or a data breach.
With the advent of COVID-19, more and more people had to embrace an alternative way of working. This 'new normal' requires many of us to;
- Work from home in less secure environments
- Understand and vet whether a request is legitimate or not
- Try to do your best by your clients and keep their data (and yours) safe
We're going to take a deep dive into how you can keep your data secure in these uncertain times, how to identify if you're being targeted, as well as some best practices to keep you, your business, and your data safe.
Why The Increase of Data Security Threats?
You've probably seen movies about hackers breaking into systems and ransoming the business in charge of that data for exorbitant amounts of money to recover it. In the same way, ransomware attacks have been on the rise since March of 2020, and they've tended to happen at the worst time possible.
Some of the reasons for the dramatic uptick of these data security incidents are due to:
- Reduced spending from consumers, which means groups that typically go after credit card details need to find new income sources
- Organised crime groups see an opportunity to target desperate organisations
- Opportunistic reconnaissance identifying vulnerabilities, possibly related to rapidly stood-up remote working practices
Take for example some ransomware attacks that occurred in the UK on May 20th 2020, involving over 150 organisations globally that had their data published on leak sites. An overwhelming majority (80%) of these were leaked after 23 March, when the lockdown first began in the UK. You can see a breakdown of the specific sectors that were the victim of ransomware in the pie graph below.
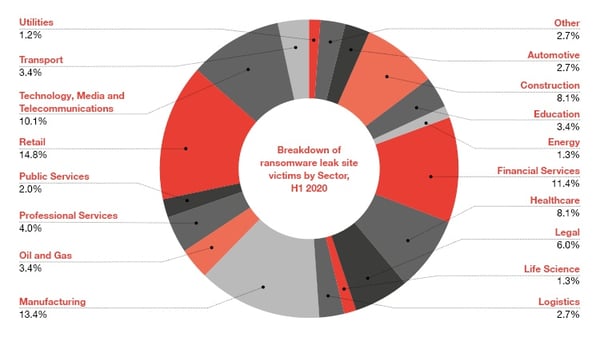 Figure 1: Breakdown of Ransomware leak site victims (courtesy of PWC)
Figure 1: Breakdown of Ransomware leak site victims (courtesy of PWC)
According to PWC in the UK, this ransoming of systems means that companies immediately lose critical business functions at a critical time. On top of that, leaking data adds a huge variety of external pressure and increases attention from information regulators.
The stress of dealing with COVID-19 is one thing, but the last thing companies want is to have their abilities to protect their customers' and their employees' data questioned, especially when there are GDPR fines to be considered.
We can draw the conclusion that the main reason so many of these threats have taken off is because there is so much uncertainty in businesses worldwide, and hackers are smartening up to how they can take advantage of desperate people and situations.
What Are These Threats?
There have been a number of targeted campaigns that cyber criminals have been responsible for, and the stats below demonstrate just how widespread these are.
- Cyber attacks were most prevalent in the healthcare and financial industries, with "healthcare cybersecurity breaches costing an approximate $7.13 million."
- In addition to this, "data breaches in the healthcare industry rose by 58% in 2020."
- Data security threats exploded in 2020, with "scams increasing by 400% over the month of March, making COVID-19 the largest ever security threat."

How To Identify A COVID-19 Phishing Threat
1. Phishing Emails
According to Google, Gmail blocks over 100 million phishing emails and these have particularly increased due to COVID-19. Phishing attacks and scams utilise fear and financial incentives to drum up a sense of urgency to try and get a user to respond. These emails can include sketchy links, suspicious attachments and also sound a bit off, especially if they appear to be sent from work colleagues' email addresses.
Some of the most common types of these emails as identified by KPMG include the following:
- COVID-19 themed emails which have malicious Microsoft documents attached to them and exploit a known Microsoft vulnerability to run malicious code.
- COVID-19 themed emails which attach macro-enabled Microsoft word docs which contain health information which can trigger a user to download Emotet or Trickbot malware
- Multiple phishing emails which lure users to go to a fake version of the Centre for Disease Control (CDC) website and then input their credentials and passwords
- Phishing emails purporting to come from government entities such as the World Health Organization (WHO) or Ministries of Health which have malware embedded into their pages
- COVID-19 tax rebate phishing which can lure and encourage recipients to browse a fake website that collects financial and tax information from unsuspecting users
These emails could look anything like the image below: (courtesy of Google Cloud)
Fortunately, there are ways to tell if an email sent to you is suspicious. Keep an eye out for the following:
- Bad grammar, punctuation and spelling
- The design and quality of the email isn't good
- The email isn't addressed to you by name and uses generic terms like "dear colleague," "dear friend," "dear customer," etc.
- Includes a veiled threat or a false sense of urgency
- Asks you for personal or financial information
- The email tone of voice is way off of how your colleague usually sounds
- The email address that the sender has used looks odd
2. Suspicious Text Messages
There have been reports in Australia that COVID-19-themed scam texts have been circulating, which claim to direct people to testing facilities. This is not legitimate and may possibly install malicious software onto your device that is designed to steal personal and financial information.
3. Webcam Extortion Emails
There have been some emails going round which demand that recipients pay up to the sender of the email, otherwise the hacker threatens to circulate video footage of the recipient in compromising positions. While it is a common scam, COVID-19 has been mixed in to this now which threatens that unless the ransom is paid, they will spread coronavirus to their family. While these wild claims are baseless, it's important to remember not to panic nor engage with such emails if you do encounter one.
4. Fake Coronavirus Maps
Security researchers have identified amongst these phishing schemes a new campaign where attackers apparently claim to have a 'coronavirus map' app that people can download onto their devices. Instead of being legitimate, the application is malware and designed to steal sensitive information from the device it is downloaded onto, including personal and financial details and passwords.

Secure Your Data Like A Boss
With all of these scams going round, it's critical to realise that data security is a huge problem if you don't have it under control. Hackers are wising up to new ways to get around security systems, and that's something you need to bear in mind.
The good news, however, (bet you didn't see that coming!) is that businesses too are learning that this is a slippery slope - and ever since the advent of COVID, cybersecurity budgets and priorities have shifted to become much more important than they once were, and in some industries, this will significantly increase (see exhibit below courtesy of McKinsey below).
.png?width=600&name=COVID-19%20cybersecurity%20spending%20by%20industry%20graph%20(McKinsey.com).png)
What's also crucial to remember is that data security doesn't just apply to individuals or departments, but rather the company as a whole. We have a couple of recommendations for you as to how you can upskill your employees, seek out best practices as well as be able to identify a potential scam. Remember, everyone needs to be in on this together, with the right skills and software to perform their jobs securely and effectively. All it takes is one person's mistake to bring the entire ship down.
A Quick Fire Guide to Reducing Your Data Security Risk
1. Do A Security Audit
To improve your data security approach, start with a security audit. For anyone who has access to your database, do the the following:
- What are your current security policies?
- Do you have a password policy?
- Is your team definitely following your policies?
- Who are your high-risk users?
- Are there measures you can take to tighten your security?
Go through each of these thoroughly and be tough on yourself. Any changes you make now will safeguard your brand, reputation and information in the future.
2. Tighten Up Your Password Security
Using your pet's name or the 'password123' is just not going to cut it. You need to use more secure passwords that involve a combination of letters, numerals, characters and the works to make it very complex and difficult for any would-be hackers to access.
Use password management tools such as LastPass to help you manage and share passwords securely, as well as giving you an audit of the password quality across your team.
While the world has slowed down in response to COVID, there's really no time like the present to finally tighten up the ship and get a password policy sorted.
3. Know the Signs of Spoofing & Phishing Attacks
Hackers are currently leveraging the uncertainty and panic by targeting remote workers and businesses with spoofing and phishing attacks. If you're a brand with any kind of reputation, you'll want to do everything in your interest to safeguard that good name. This means that you should be aware of the types of attacks that are being commonplace and the signs of an attack.
Over the course of 2020, there has been a significant increase of fake password change requests. Essentially, hackers are sending look-alike password requests via email, and they're going out of their way to make it look as legitimate and sophisticated as possible. This means you need to be on your A game as much as you can when it comes to dealing with fishy requests, and also to think before you take action!
4. Have a clear onboarding and off-boarding process
This needs to include the following:
- The process to request new users are set up, changes to users and the removal of employees
- Clear guides that are regularly reviewed for permissions, roles, teams, etc, per platforms
- Ownership and training for anyone managing onboarding and off-boarding, including back-ups for when these individuals are away
5. Limit import and export functions in your various apps
- This could be updated within the spreadsheet section
- Export functions allows your data to be stolen by hackers or disgruntled employees
- Import functions could seriously mess up your data is someone does not know what they are doing, which could cause hours of fixing if someone imports the wrong data to the wrong place, or dependent on your platform may be impossible to retrieve your original data
- Import functions can also be used by individuals to import stolen data and use your brand and platforms to send phishing emails, compromising your brand
6. Say Sayonara To Spreadsheets
These can become out of date very quickly if your data isn't integrated and live, or if you're working in Excel (without 365) or a non-collaborative tool. It can be tricky to filter and see when things were last updated, especially if users are not aware of the features that allow them to do this.
Spreadsheets are a real security risk and if the information they hold is stolen and leaked, it's not going to be a pretty situation. Fortunately, there are some amazing dedicated tools available that will streamline your processes, tighten your security and use live and integrated data in ways that a shared spreadsheet wouldn't be able to.
7. Enable Two-Factor Authentication
This is a crucial step to prevent unwanted hackers from being able to access your accounts. It's one thing to get through to your email but if you have two-factor authentication enabled to send a code to your phone number to prove it's you, it's not going to be a cakewalk for a potential hacker.
8. Use a Password Manager
There are plenty of great password managers out there including LastPass, Dashlane and Keeper Password Manager & Digital Vault. With a password manager, it removes the hassle of having to remember every single password you've ever come up with and provides a safe vault where your passwords are stored (and it even helps you generate new and super secure passwords for future requirements).
9. Review Access Levels
No matter what platform you're using, it pays to be very aware of the access levels that each employee of your business has. You don't want everyone in your company to have access to highly sensitive material (unless it concerns them.) Be sure that you often review what your employees can access, what documents and files they can change, and what they can do with the information you have. Be sure to limit any areas that could cause undue risk including importing, exporting and admin.
10. Use Single Sign-On Wherever Possible
Single sign-on (SSO) is an authentication method that enables users to securely authenticate with multiple applications and websites by using just one set of credentials. It works based upon a trust relationship set up between an application and an identity provider. It's a very powerful system that frees up businesses from needing to hold passwords in their databases, reduces login troubleshooting, and also decreases the damage a hack can cause.
11. Run Regular Security Training
Training your staff to understand the kinds of security risks your business could face is critical. It will help them to become more aware and better at spotting potential attacks, as well as informing them how they can stay safe when conducting business online. By implementing regular security training, you'll show your team how important cyber security is, why what you're doing to secure your business online is important, as well as what this all means for them and what they need to do to ensure it is not compromised.
12. Review Your Platforms
With platforms becoming more and more dominant in business and software architecture, they too are at risk of being compromised. Because so many of these are cloud-based and software-defined, you need to analyse how secure these platforms are. Check if the security measures on these are up to par, and in the event they are not, update them accordingly to be more secure.
13. Run Inter-Business Competitions
This is a great way to encourage employees to have fun and simultaneously become more aware at what could constitute a hack, and also what to look out for on a day-to-day basis. Set up a challenge that can run for a month, a week, etc. Organise your business into teams and make it so that whichever team has the best 'hack' (an ethical one of course), wins a prize. This way, you're gamifying the concept of cyber security and up-skilling your employees to keep your business safe.
14. What Can You Do?
The main thing is to be vigilant and double-check any request you're receiving. Look at who the sender is (especially the sender's details), give your client, partner or software service a call to make sure that it's legitimate before entering any information, and share the information around the increase in attacks.
Be sure to look out for these if you suspect a scam:
- Misspellings and poor grammar
- Suspicious looking links
- The design and quality of the email is strange
- The sender's tone of voice sounds 'off'
- There is a veiled threat or false sense of urgency
- The sender is demanding personal or financial information
- Does it sound too good to be true? Probably is!
How Integration Fox Can Help You
When it comes to data security, take one more thing off your mind. Integration Fox allows you to sync your platforms and integrate your data, without worrying if you're potentially compromising its integrity. Consolidate your data and set you and your team up to make better informed business decisions in a safer and securer way.
If you're interested to learn more about how Integration Fox can solve your integration problems while also increasing your data security, get in touch, we'd love to talk to you.